The following sequence diagram describes what happens when a user wants to access an application protected by the Identity and Access Proxy:
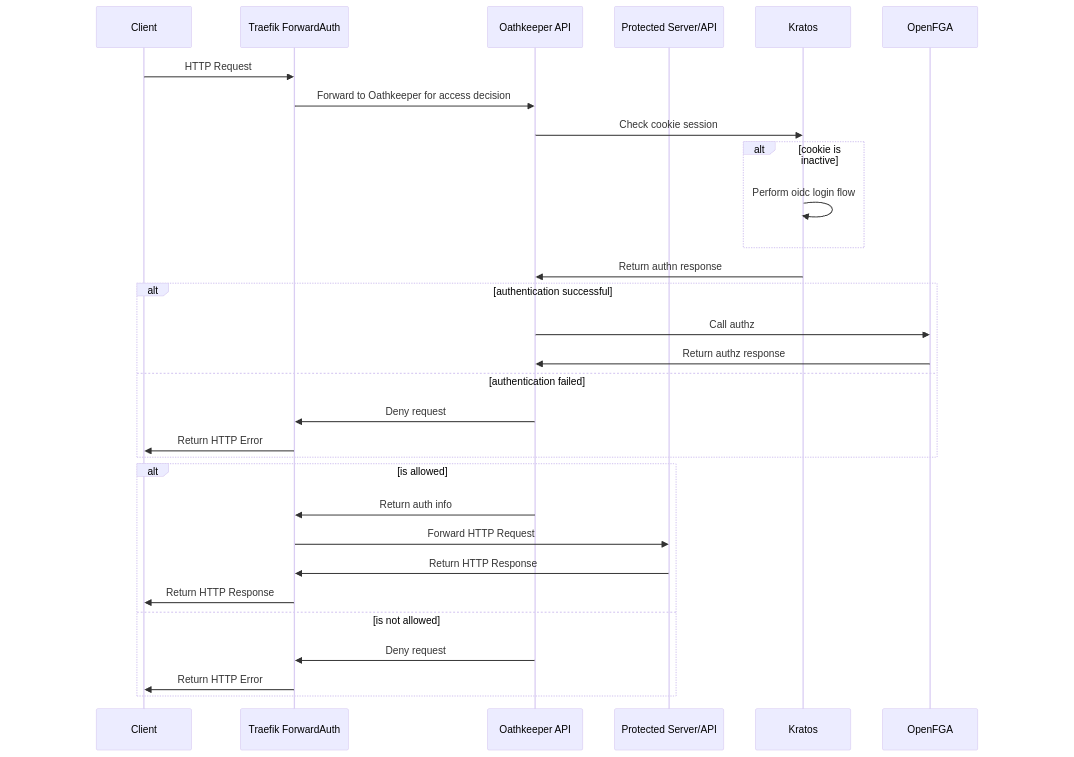
The following sequence diagram describes what happens when a user wants to access an application protected by the Identity and Access Proxy:
