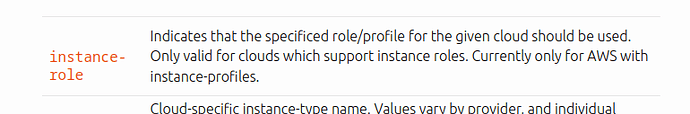
I am attempting to utilize this feature
https://discourse.charmhub.io/t/constraint/6184#heading--instance-role
where in which I call out a IAMRole by name, that I want attached to the juju charm I am instantiating… however when I deploy nothing is getting attached…? Did i misunderstand the feature ? Here’s how i am attempting to use it
mahrio:
charm: mahrio
channel: latest/beta
num_units: 1
to:
- "2"
options:
git_deploy_private_token: "SOMETOKEN"
mahrio_deployment_name: "SOMEDEPLOYMENT"
mongodb_connection_str: "mongodb+srv://some_password"
messaging_from_email: "contact@some.place"
sqs_target_url: "https://some_url_at_aws.com"
bindings:
"": my-public-subnet
instance-role: "MYCOOL-ROLE"
I tried changing the permissions to give full IAM access but this doesn’t seem to have any effect.
EDIT: One other question… there’s no way in Juju to set additional Security Groups … besides what Juju sets by default… correct ? I set expose 80 and expose 443 but still must manually go and append a security group which opens these for traffic… would be great to have that automated in AWS but I understand if not possible rn.
EDIT2: Ah I just read the last sentence of that feature… so I must have had to used a controller and bootstrapped it with the instance-roles ala Using AWS Instance Profiles With Juju 2.9 ? The issue with that is I am using JaaS aka Jimm controller… so I guess if I want to utilize this feature I must migrate to my own controller…?